In my opinion it's not interesting part of the contest to write algorithms you have already written dozens of times. I kind of see why people who prepare to IOI/ICPC would do that, but not other participants. So I created yet another tool that allows to use your own library locally and submit to CodeForces. Idea is that you write in one file, then submit another file and you don't need to do any other action to actually generate file to submit (once everything is configured)
Demo
The tool consists of two independent parts
inline_includes: this is a simple python script that inlines all the includes you used from whitelist of directories (so that standard headers such as are not inlined). It's far from supporting whole c++ (e.g it doesn't support #include MACRO) but it was enough for my library. This part can be replaced for your own language. The paths to directories to inline is passed
command_fs: this tool is written in c++ using libfuse. It accepts to directories (mount point and source directory) and a command (With arguments). So for each file file in source directory it virtually creates file file is the mounted directory with the content of output of command command args file. So, if you pass inline_includes as a command it "replaces" all the files with its contents with inlined includes
OS Support:
MacOS: I tested on 10.14 and 10.15
Linux: It should work but I haven't tested
Windows: I don't know much about windows but in principle it should work via fuse api of WinFSP
Installation:
inline_includes:
From brew:brew install AlexeyDmitriev/sp/inline_includes
Manual:
It's just a python file, you can grab it from github in the most convenient for you way.
command_fs:
From brew:
brew cask install osxfuse # Required because formula can't depend on cask in brew
brew install AlexeyDmitriev/sp/command_fs
Manual:
1. Install libfuse in someway
2. It's a cmake project, you can get it from github and build as usual:
mkdir build
cd build
cmake ..
make
Then binary called command_fs is what you need
I'll appreciate help to package this for your own platforms.
Usage
So, first you create a virtual filesystem (assuming both command_fs and inline_includes are in $PATH, otherwise you can replace them with a path to them)
command_fs /path/to/mount_point /path/to/sources/you/write inline_includes /include/path1 /include/path2
Then, all the files from /path/to/sources/you/write are inlined in /path/to/mount_point and you are ready to enjoy problem solving
Once you are done you can unmount the directory using umount /path/to/mount_point (but you don't have to)
Also you should be able to configure automount so that you don't need to run anything after reboot but I've never tried that.
Any comments are welcome









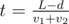 seconds. The moment when width gets a value of
seconds. The moment when width gets a value of 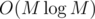 and entire solution in
and entire solution in 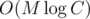 or
or 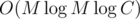
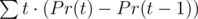 .
. 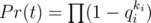 , where
, where 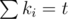 ).
).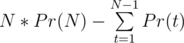 . So it is enough to prove that:
. So it is enough to prove that: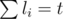 ), not equal to set produced by greedy algorithm
), not equal to set produced by greedy algorithm 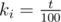 , it gives probability of end of the game not less than optimal. Then
, it gives probability of end of the game not less than optimal. Then 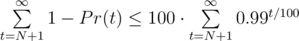 . It could be estimated as sum of geometric progression. If
. It could be estimated as sum of geometric progression. If 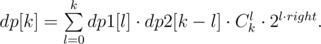
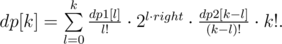
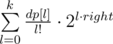 and
and 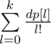 . We can obtain the coefficients of the first polynomial from the coefficients of the second in
. We can obtain the coefficients of the first polynomial from the coefficients of the second in 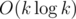 . So, we can compute this dynamic programming for all lengths — powers of two, in
. So, we can compute this dynamic programming for all lengths — powers of two, in 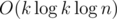 , using the fast Fourier transform. In fact, it is more convenient to compute
, using the fast Fourier transform. In fact, it is more convenient to compute 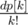 using the same equation. After that, we can use the same merge strategy to compute the answer for the given
using the same equation. After that, we can use the same merge strategy to compute the answer for the given 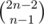
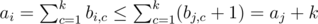
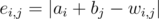 .
.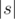 , we will calculate the sum of simple pretinesses of all substrings of that length, let’s call it
, we will calculate the sum of simple pretinesses of all substrings of that length, let’s call it 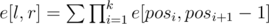 where the sum is taken over all partitions of the segment
where the sum is taken over all partitions of the segment 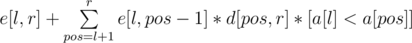 ([statement] is equal to 1 if the statement is true, 0 otherwise) and
([statement] is equal to 1 if the statement is true, 0 otherwise) and 
